by John Zorabedian on October 20, 2015
https://nakedsecurity.sophos.com/2015/10/20/facebook-to-warn-you-of-targeted-attacks-check-this-security-setting-anyway/
Facebook has announced that it will notify users it suspects are being targeted by nation states and urge them to take extra security precautions.
Alex Stamos, Facebook’s chief security officer, explained the new notifications in a 16 October blog post, saying users will only receive the warnings if Facebook has strong evidence suggesting they are being targeted by nation-state sponsored attackers.
If the social network believes you are under attack from state-sponsored hackers, it will show a pop-up message in your feed explaining that you may have been targeted.
The message asks, but does not require, those users to turn on an extra layer of protection for their account called Login Approvals.
Stamos said Facebook “will have always taken steps to secure accounts that we believe to have been compromised,” but will show the warning to users because these attacks may be “more advanced and dangerous” than others.
This is how the message looks in the desktop version of Facebook:
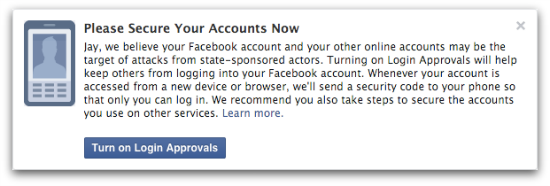
Jay, we believe your Facebook account and other online accounts may be the target of attacks from state-sponsored actors. Turning on Login Approvals will help keep others from logging into your Facebook account. Whenever your account is accessed from a new device or browser, we'll send a security code to your phone so that only you can log in. We recommend you also take steps to secure the accounts you use on other services.
Because of the persistence of state-sponsored attackers, anyone whose Facebook account is under attack by a nation state is probably also being targeted on other services, so Facebook encourages securing those accounts as well.
Google began sending similar warnings to Gmail users back in 2012.
Just like Google, Facebook says it can’t reveal how or why it suspects state-sponsored attacks, for fear of giving away useful information to attackers about security methods.
Nation states may target individuals for political or national security reasons, but also attack individuals to gain access to their employers’ intellectual property or customer data, for example.
Countries like North Korea and China have been suspected of sponsoring attacks on private companies.
Hackers affiliated with the Chinese military were indicted by the US two years ago for allegedly hacking into several US steel companies.
The US claims the Chinese hackers used phishing emails and malware to gain access to email accounts of company officials, in order to steal information that would benefit Chinese state-run steel companies in trade disputes.
Targeted or not, extra security is always a good idea
Even if nation states aren’t likely to target you personally, it would be a shame to fall into the trap of thinking “no one’s interested in little old me.”
As Naked Security expert Paul Ducklin pointed out in a post describing all the bad excuses we make for neglecting our security, we are all on cybercriminals’ radars:
We're all in the sights of cybercrooks somewhere, and we owe it to ourselves and to everyone else to do the best we can to thwart them.
Today’s cybercriminals are typically in the business of making money, and to do that they want to compromise as many users and devices as possible.
One method for attackers to gain access to your accounts is to implant malware on your computer that can steal passwords.
Malware of this sort can get on your computer in various ways, such as through boobytrapped email attachments, or by visiting a malicious website harboring malware that downloads automatically (called a drive-by download).
Malware can also spread via Facebook.
We recently learned of a hacker using a type of malware called a “Facebook Spreader” to compromise Facebook accounts via malicious links in Facebook chat messages.
In August, a US-based hacker named Eric Crocker pleaded guilty to spreading Facebook malware to hijack thousands of accounts in order to send spam.
Just like Facebook recommends, we think it’s a good idea to add extra layers of security to your accounts, such as login verification or two-factor authentication.
Even if you’re not likely to be a target of a nation state, that’s no reason to become easy prey for common cybercriminals.
How to turn on Facebook Login Approvals
When you turn on Facebook Login Approvals, you’ll need to enter a special one-time code whenever you log into Facebook from an unrecognized device or browser.
You’ll receive the codes on your phone as a text message, so Facebook needs your mobile phone number to send Login Notification alerts.
Login Approvals are similar but more secure than Login Notification, which alerts you when your account is accessed from a new device or browser, but without requiring a code.
To turn on Login Approvals:
- Click the down arrow at the top right of any Facebook page
- Go to Settings > Security
- Click on Login Approvals
- Check the box and click Save Changes
Finally, once you’ve set that up, make sure you change this setting so you can’t be searched for by phone number.